TRANSPARENCY REPORT 2021 BIT B.V. - VERSION 2023-02-03
In 2012, BIT released its first transparency report with the goal of providing insight in how frequently we receive requests for our customers' personal data, how often we process notice-and-takedown requests, and how many Responsible Disclosure notifications we receive. This report contains information for the year 2021.
We share this information to demonstrate transparency to our partners and interested parties, as privacy concerns continue to rise in importance. To highlight trends, we have included data from 2017 through 2021 in the report. Additionally, we can provide data from before 2017 upon request.
For each category, the report outlines the number of complaints, requests, and notifications received, as well as how they were handled.
Personal Data
Below you will find an overview of the different types of requests BIT has received with regard to the handover of personal data, and how these requests were handled.
Disclosure of Personal Data
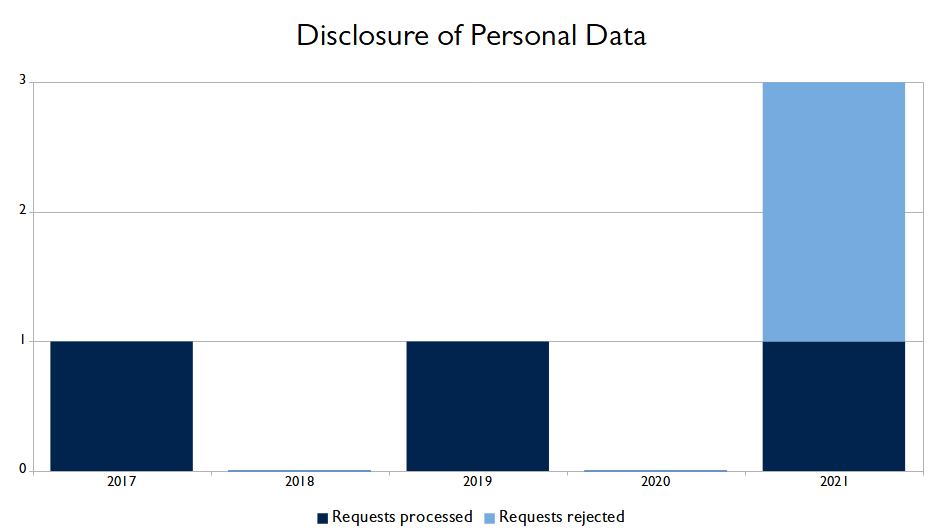
The table below shows the number of requets that BIT has received to disclose customers' personal data to law enforcement agencies. The table also indicates whether BIT complied with the requests or not.
| 2017 | 2018 | 2019 | 2020 | 2021 | |
| Requests processed | 1 | 0 | 1 | 0 | 1 |
| Requests rejected |
0 | 0 | 0 | 0 | 2 |
| TOTAL | 1 | 0 | 1 | 0 | 3 |
We have included the number of requests in the graph below to provide a clear overview of the annual developments.
Reporting Personal Data Breaches
By law, BIT must report any personal data breaches that occur. In 2021, there were no incidents that required BIT to report.Previous reports of personal data breaches in 2017 and 2018 were due to the loss of an employee's phone, which had access to the employee's company email account. In both cases, the phone was password-protected and encrypted.
| 2017 | 2018 | 2019 | 2020 | 2021 | |
| Reports of personal data breaches | 1 | 1 | 0 | 0 | 0 |
Legal Interception Orders
The National Police, FIOD-ECT, Netherlands Labour Authority, IOD, AID, AIVD and MIVD have the authority to issue orders to a provider to perform interception or wire-tapping. This can be an email tap or IP tap. The table below shows the number of interception orders that BIT has received.
| 2017 | 2018 | 2019 | 2020 | 2021 | |
| Interception orders received | 2 | 0 | 0 | 0 | 0 |
Takedown Requests
In this section you can find an overview of the various takedown requests BIT has received and how these requests were handled.
Takedown Requests Regarding Malware
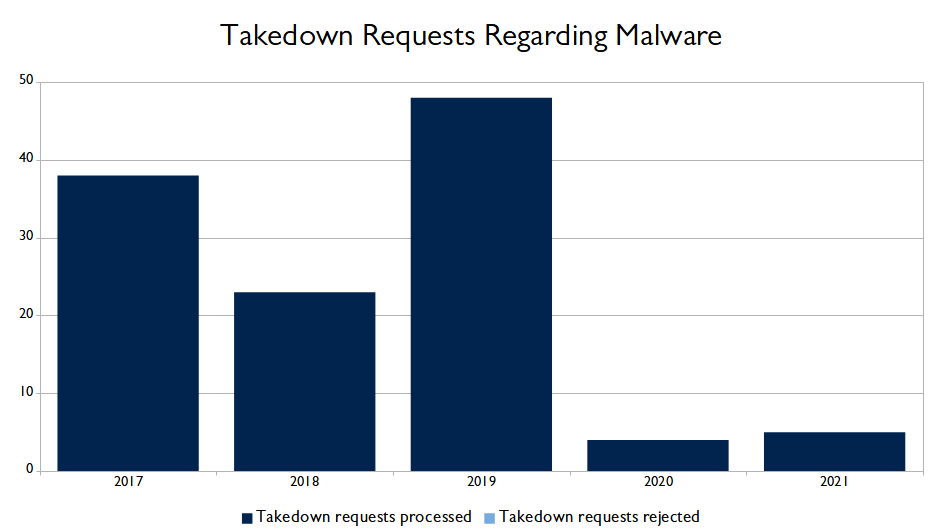
The table below provides an overview of the number of takedown requests BIT has received for hosting (suspected) malware, as well as how these requests were handled.
| 2017 | 2018 | 2019 | 2020 | 2021 | |
| Takedown requests processed | 38 | 23 | 48 | 4 | 5 |
| Takedown requests rejected | 0 | 0 | 0 | 0 | 0 |
| Total | 38 | 23 | 48 | 4 | 5 |
We have included the number of takedown requests regarding malware in the graph below to provide you with a clear overview of the annual developments.
Takedown Requests Regarding Copyright Infringement
In our 2013 Transparency Report, BIT included the number of notice-and-takedown requests received for alleged copyright infringement for the first time. The table below displays the figures for the past five years.
| 2017 | 2018 | 2019 | 2020 | 2021 | |
| Takedown requests not processed | 2000 | 1472 | 921 | 372 | 19 |
| Takedown requests rejected | 0 | 0 | 0 | 0 | 0 |
| Takedown requests forwarded | 0 | 14 | 4 | 53 | 221 |
| Total | 2000 | 1486 | 925 | 425 | 240 |
We have included the number of takedown requests regarding copyright infringement in the graph below to provide you with a clear overview of the annual developments.
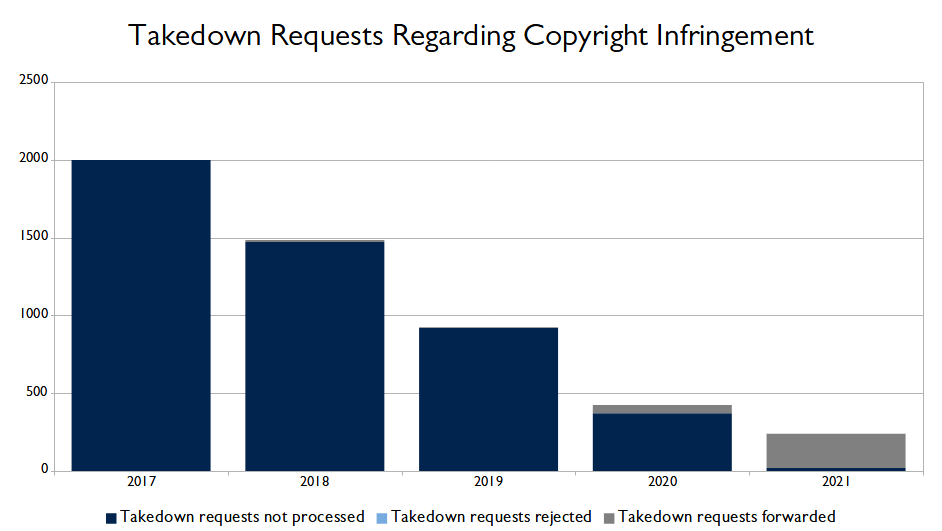
Until 2020, the majority of requests not processed were automatically filed by a small number of parties on behalf of the film and music industry. At that time, these requests did not comply with our notice-and-takedown procedure.
Takedown Requests Regarding Phishing
The table below provides an overview of the number of takedown requests BIT has received regarding phishing, as well as how these requests were handled.
| 2017 | 2018 | 2019 | 2020 | 2021 | |
| Takedown requests processed | 103 | 81 | 82 | 75 | 17 |
| Takedown requests rejected | 0 | 0 | 0 | 0 | 1 |
| Total | 103 | 81 | 82 | 75 | 18 |
We have included the number of takedown requests regarding phishing in the graph below to provide you with a clear overview of the annual developments.

CSAM
The table below shows how many takedown requests BIT has received regarding CSAM (child sexual abuse material), and how these requests were handled.
| 2017 | 2018 | 2019 | 2020 | 2021 | |
| Takedown requests processed | 0 | 0 | 0 | 0 | 0 |
| Takedown requests rejected | 0 | 0 | 0 | 0 | 0 |
| Total | 0 | 0 | 0 | 0 | 0 |
Responsible Disclosure
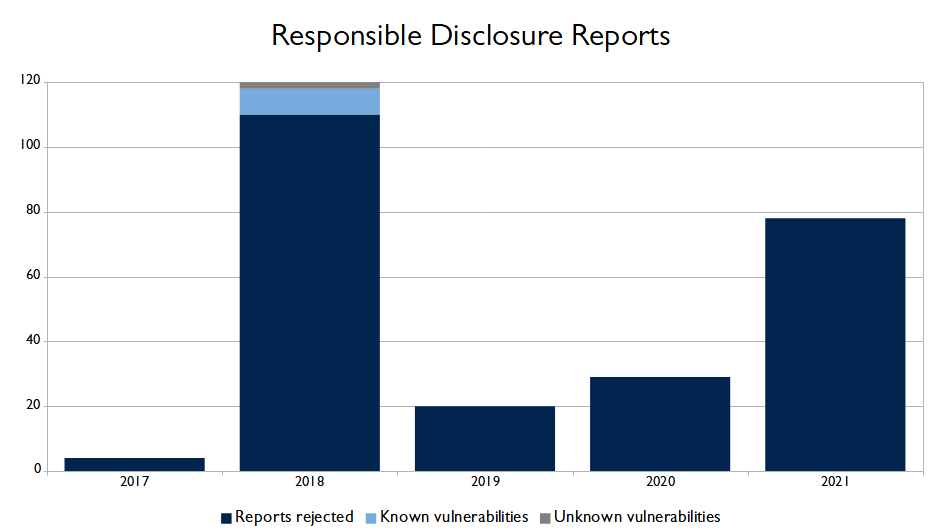
In the table below, you can see the number of Responsible Disclosure reports that BIT has received. We have distinguished between rejected reports, vulnerabilities that were already known to us, and vulnerabilities that were not previously known to us.
| 2017 | 2018 | 2019 | 2020 | 2021 | |
| Rejected reports | 0 | 110 | 20 | 29 | 78 |
| Known vulnerabilities | 0 | 8 | 0 | 0 | 0 |
| Unknown vulnerabilities | 0 | 2 | 0 | 0 | 0 |
| Total | 4 | 120 | 20 | 29 | 78 |
We have included the number of Responsible Disclosure reports BIT received in the graph below to provide you with a clear overview of the annual developments.
Conclusions
BIT does not provide services to private customers, which is why the number of requests for personal data and the number of legal interception orders remain low. In 2021, we did not receive any orders for legal interception.
The number of reported malware infections has significantly decreased in 2020 and 2021. This may be due to the reporting of these infections through other classifications, such as RBL listings.
The number of copyright infringement reports has again decreased. However, since 2021, BIT does forward complaints from parties making these complaints on behalf of the film and music industry, which explains the rise in the number of forwarded requests.
Since 2019, we have decided not to mention any monetary compensation in our Responsible Disclosure policy. As a result, the number of reports after 2018 has decreased. However, we still receive a relatively high number of reports on issues that are intentionally made public and where deliberate choices have been made for settings, or where vulnerabilities have been identified from version numbers even though backports have been used. Additionally, we also receive reports on systems that are excluded from our Responsible Disclosure policy, such as customer systems. We do forward these reports to the respective customers.

